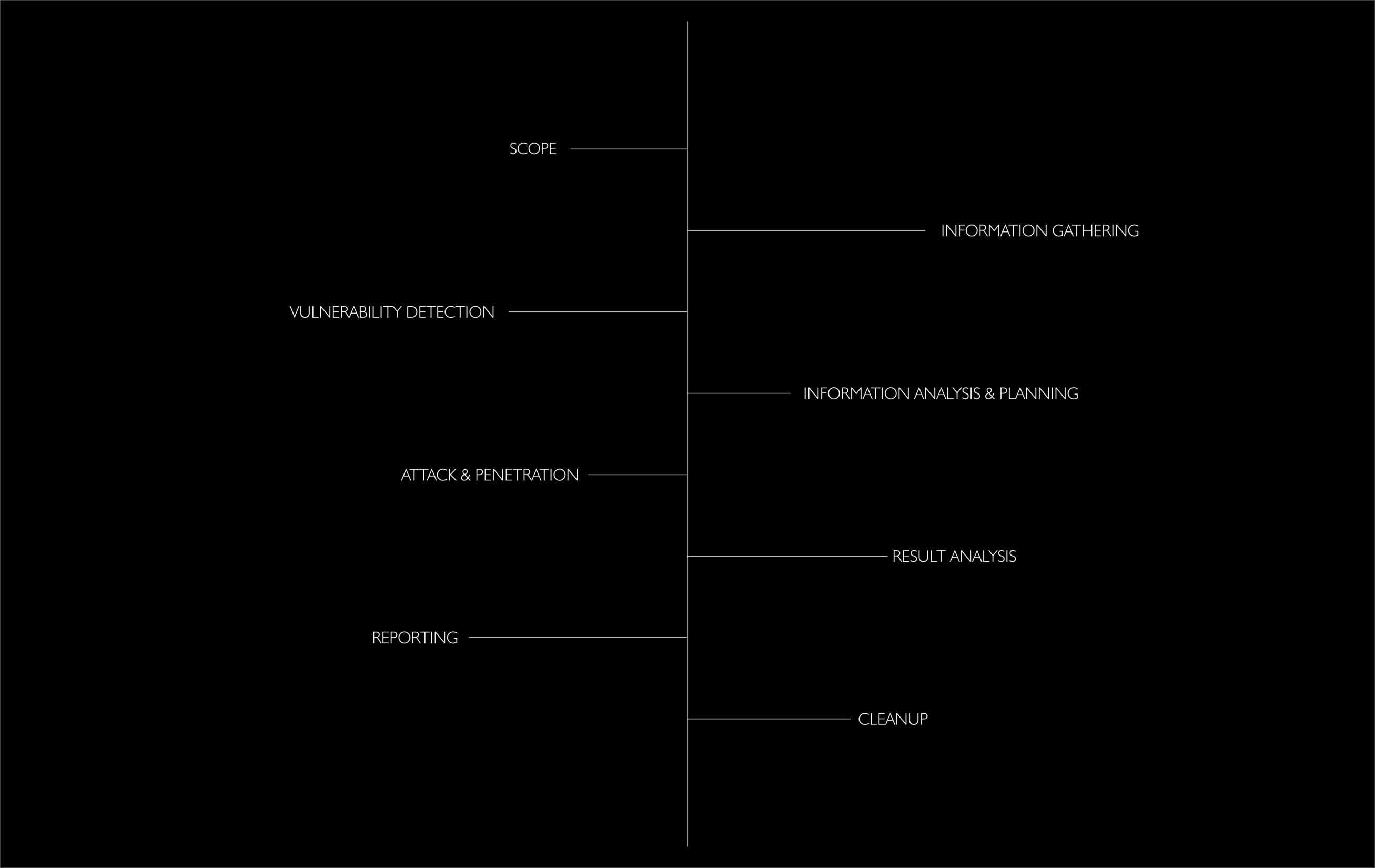
Web applications are mostly prone to different vulnerabilities that may provide access to hackers. This test will harden the security of web applications and identify the vulnerabilities in the applications which will prevent it from being hacked.
Most of the mobile applications & web applications uses API for exchange of data. This test covers the entire API which includes all the endpoints. We will test each and every endpoints to identify security vulnerabilities that may affect the company or the customers of the company.
IOS applications are mostly vulnerable to attacks that could result in a data breach. We will perform tests against a given iOS application to identify security holes that could affect the iOS App users and the service provider.
Android applications are mostly vulnerable to many attacks that could affect the user or the target company. We will perform security tests against the application and its source code to identify security vulnerabilities and things that could result in a compromise of the company information and its customers.
Hosts within the network often runs services that have security holes. We will test the entire network to identify every possible flaw that could affect the hosts of the network. Each host will be covered in this test and the network security will be hardened.
There are often some mistakes in the source codes that could leak to multiple vulnerabilities. We will perform a code review against the given source code to identify security vulnerabilities and things that could possess a risk to the company. The fixes and patches will be given based on the code provided.
HACKERSRAY
CEO
Penetration Tester
Penetration Tester
Penetration Tester
Penetration Tester
Penetration Tester
Penetration Tester
Penetration Tester
Hackersray
In an organisation, security is an aspect that might be ignored sometimes. As most companies think its an unnecessary part. Thats the reason, these companies get hacked and result in a data breach. Top companies like Google, Facebook and Yahoo etc take security seriously but still there are severe vulnerabilities identified every year that could result in a data breach. Protecting the company's infrastructure and the application is important as this could result in the loss of client's trust and their confidential data if hacked. Protection of a company should be taken seriously as this could destroy a well-running company. Penetration testing should be performed on all areas before a malicious hacker could get advantage of it. Testing security of a company and hardening it protects the company from cyber-attacks and as well as data breaches. Protect yourself before you get hacked by the Malicious Hackers.

We have worked with Hackersray for several months as part of our bug bounty program, and have been very impressed with not only their timely communication and ability to find vulnerabilities, but also explain them in an easy to digest format. Hackersray has had more success than third party companies that we have hired, and we have found value with both their ability to test and retest after the vulnerabilities have been remediated.

Hackersay did a great security review of our software. Even after 3-4 previous reviews by other security teams this year, Hackersray found more than 10+ critical and medium XSS breaches that makes his team stand out on the market in quality. Thanks to his team, our customers feel more confident in data protection using our software.

Your service is good overall, worth the cost. The core work, test was good, discovering flaws in not only technical but also business logics. We can see you were enthusiastic in your work when asking to start as soon as possible and to pentest on as many subdomains as possible.